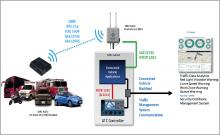
The technological developments enabling connected and automated vehicles (C/AVs) and Vehicle to Everything (V2X) communications are providing new mobility capabilities and safer roadways. These developments in particular are allowing vehicles to communicate with other vehicles, roadside infrastructure, pedestrians, and other users, driving real-time flow of data and collection of performance measures.
This new level of connectivity and communication is helping deliver on the C/AV and Smart City’s promise of Vision Zero and a more sustainable future. The C/AV wireless communications, either dedicated short-range communications (DSRC) or C-V2X (cellular V2X), along with connected traffic management systems, are indeed helping improve safety and optimise mobility.
With that kind of upside, what’s the concern? The integration of wireless communications with increasingly network-connected surface transportation and traffic management systems now exposes each system to the vulnerabilities of the others, greatly increasing potential threat surfaces.

There are more than 400,000 traffic signals deployed throughout the US.
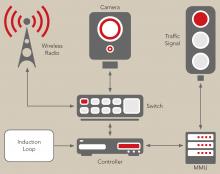
Without a doubt, traffic signal controllers and management systems play a critical role in the safety of millions of people and the security of the infrastructure. Traffic signal controllers were originally designed for hardwired private serial communications, which isolated them from wider connected networks and largely shielded them from malicious system intrusions. However, as the demands in traffic management capabilities increased, so did the technological demands on the traffic controllers. Today’s traffic controllers integrate with an array of sensors and devices at the traffic intersection, as well as communicate with other controllers and central traffic management systems over the Centre to Field (C2F) network.
Physical security
Modern traffic management systems also integrate with a variety of other systems and subsystems, including systems for C/AVs, monitoring and surveillance, transit and emergency management. While the enhanced connectivity between different systems has enabled new capabilities in managing and optimising traffic control, it has also exposed these once-isolated systems to network accessibility and made them vulnerable to security threats.
Attack surfaces have grown manifold. As traffic management systems continue to evolve and become networked with greater complexity, the security aspect of these networks and systems requires more focus and attention. In view of the ever-growing connectedness enabled by Internet of Things (IoT) technologies and the vulnerabilities they present, the industry needs to accelerate its efforts to comprehensively enhance the security of its infrastructure.
Security of critical infrastructure starts with the physical security of all hardware equipment and operational facilities. The goal is to detect and prevent physical intrusion into the devices and computers that are part of the infrastructure, including traffic cabinets and other electronic devices at traffic intersections, networking devices and critical servers related to the connected infrastructure.
It is imperative for transportation agencies to consider using secure electronic or mechanical locks on the cabinets. Electronic lock solutions with a variety of feature sets are available from several vendors. They can be programmed to provide access credentials for designated users with the option of enforcing schedule-based access, with all access events being recorded for review and audit.
In addition to secure locks, video surveillance and monitoring of field equipment provide another method to deter and catch those attempting to illegally gain access to the cabinet. Appropriate physical security measures such as video surveillance, metal detection and advanced identification should also be considered for facilities hosting critical servers and computing devices in the ITS network.
Edge vulnerabilities
All edge devices in an ITS network, such as traffic controllers, conflict monitors, sensors and roadside units (RSUs) act as IoT endpoints, and are subject to the same vulnerabilities as any other endpoint device in the IoT world.

Hardware device manufacturers should embed advanced security into all product offerings. Best practices should be followed to mitigate common hardware vulnerabilities, eliminate insecure backdoors, and make the products hardened against common attacks. Well-known hardware security solutions like hardware-based crypto modules, hardware Root of Trust (RoT) and Trusted Platform Modules (TPM) should be considered as applicable. The operating system and software applications running on these devices should also be properly hardened.
Traffic controllers, conflict monitors, sensors and RSUs should be routinely scanned for malware, vulnerabilities and undesired changes in the software. Appropriate remediations, including software and operating system updates, should be applied. All unnecessary protocols, ports and services should be disabled. All critical devices should be routinely backed up, and restoration from back-up should be tested regularly to ensure that the back-ups would be useful if needed. Access to the endpoint devices and the use of portable storage units like USB drives should be controlled and monitored.
Network security
Traffic controllers in modern ITS networks typically communicate with one another, as well as with a variety of sensors and central traffic management systems. The multi-tiered networks may combine various communication media such as hardwired fibre or copper, point-to-point or point-to-multipoint wireless, and cellular.
The best practice is to have a layered security approach for protecting network infrastructure and resources. This should include multiple layers of defence, starting at the edge of the network and implemented at various internal levels of the network. The more recent concept of the Cyber Kill Chain acknowledges the reality that intruders often get beyond well-planned defence in depth through attacks like advanced persistent threats (APTs) and recommends different defensive tactics when they do. The Cyber Kill Chain approach notes that attacks typically occur in phases from reconnaissance to data exfiltration, and that interrupting the attack during any phase in the chain protects the infrastructure and assets.
Securing the network perimeter is a fundamental requirement in network security. Network perimeter refers to the boundary between a private network and a wider, more public network – one that is exposed to a wide variety of threats. Devices like firewalls and smart firewalls should be used to restrict inbound and outbound traffic based on a set of carefully crafted rules.
Intrusion detection systems (IDS) monitor and analyse traffic in a network and detect security threats. Intrusion prevention systems (IPS) also analyse traffic in a network, but they also stop any traffic that represents a security threat. IDS/IPS devices should be used to monitor network traffic and stop known security threats, and they are particularly useful when dealing with legacy field equipment with inadequate built-in security. Within a network, network segmentation and enforcement of security policies within network segments is a very effective strategy to keep an attacker from perpetrating an attack on the entire network. Network segmentation is achieved by creating virtual LANs (VLAN), demilitarised zones (DMZ) and virtual private networks (VPN). C2F networks, field device networks and networks related to C/AV and V2X communication should be segmented and protected suitably from wider agency networks.
All devices and networks should be subject to security reviews and penetration testing to identify security gaps and vulnerabilities. Advanced security solutions like security information and event management (SIEM) systems may be used to monitor, aggregate and analyse network activity. All employees and contractors with network access should receive ongoing training on security best practices to address the human element in cybersecurity.
All data being transmitted in a network should be encrypted in order to avoid eavesdropping or interception. Unencrypted communication is vulnerable to a man-in-the-middle (MITM) attack, where an attacker can easily read and alter network packets in a communication stream. To help protect data, secure protocols should be used for file transfers. All data at rest should also be encrypted to ensure data confidentiality and integrity.
Strongest encryption
Wi-Fi networks should always be set up with the strongest encryption supported on the radios. The ideal choice would be WPA2 encryption, if available on the radios being used, but even a weaker encryption like WPA (Wi-Fi protected access) or WEP (wired equivalent privacy) is better than having no encryption at all.
For cellular networks, agencies should work with their mobile network operators (MNOs) to ensure that their network topologies are sufficiently secure, and that all network traffic is being encrypted. Trusted and dedicated communication channels like cellular VPNs may be used for secure communications. Third-party over-the-top services may also be used to provide an additional layer of security. The National Institute of Standards and Technology (NIST) Special Publication 800-187 provides very specific and detailed guidance on the security of LTE networks. Agencies should closely monitor and control the deployment of wireless devices like cellular modems and Wi-Fi dongles in traffic cabinets in order to verify that only authorised and sufficiently secured networks are permitted to communicate with the traffic control equipment, ensuring that data is not transmitted to unauthorised parties.

Identity and access management (IAM or IdAM) refers to a framework of policies and technologies used to control and monitor user access to critical system resources and information. The process involves assigning a digital identity to each entity and user in a system, providing specific roles to users through what is known as role-based access control (RBAC), and maintaining a mapping of the users and their roles and privileges using a directory service (typically managed through the Lightweight Directory Access Protocol or LDAP). Microsoft’s Active Directory (AD) is a very popular directory service for Windows domain networks.
Access to all critical resources and networks should be closely controlled. In order to access a resource, a user must be authenticated and authorised. The process of authentication verifies the identity of the user (typically via credentials like username/password, digital certificate or biometrics), while the process of authorisation checks if the user is authorised to access the resource and at what level (e.g. read, write, delete). Multi-factor authentication techniques should be considered for use, wherever applicable, as well as robust password policies - which should be implemented and enforced. All critical systems and applications should be configured for complete audit logging for the purposes of monitoring and investigation.
Transportation focus
It is strongly recommended that the transportation management industry focus on and accelerate security efforts and implementation, as well as develop more specific standards emphasising security considerations.
The industry, including product vendors, integrators and agencies has an important role to play in enhancing the security posture of the entire transportation management ecosystem. In addition to developing secure traffic control products and systems, product vendors and integrators must extend services and partnership capabilities to include support for cybersecurity assessment of agency networks and help transportation agencies and DoTs establish and achieve their security goals. It is imperative to collectively work to address this critical issue at all levels and share the common goals of a safe and secure transportation infrastructure.
The Cybersecurity Framework developed by NIST is a comprehensive guide for organisations to assess and improve their ability to prevent, detect and respond to cyberattacks. It is highly recommended that transportation and traffic management agencies work with security experts to implement the NIST framework and follow other available standards and guidelines to enhance their overall security posture. The process starts with a comprehensive security assessment and risk analysis to determine the security gaps and degree of vulnerability, followed by the development of necessary mitigation plans and the time-bound implementation of all action plans.
Some transportation agencies have already taken steps in this direction, and others are expected to follow. Security is a complex subject and adhering to security standards and best practices often involves some perceived inconvenience in day-to-day operations. However, it is very important to remain focused on improving the security of critical transportation management infrastructure and enable it to withstand, as well as rapidly recover from, all physical and cyber hazards.
ABOUT THE AUTHOR:
Sunny Chakravarty is Econolite VP of engineering